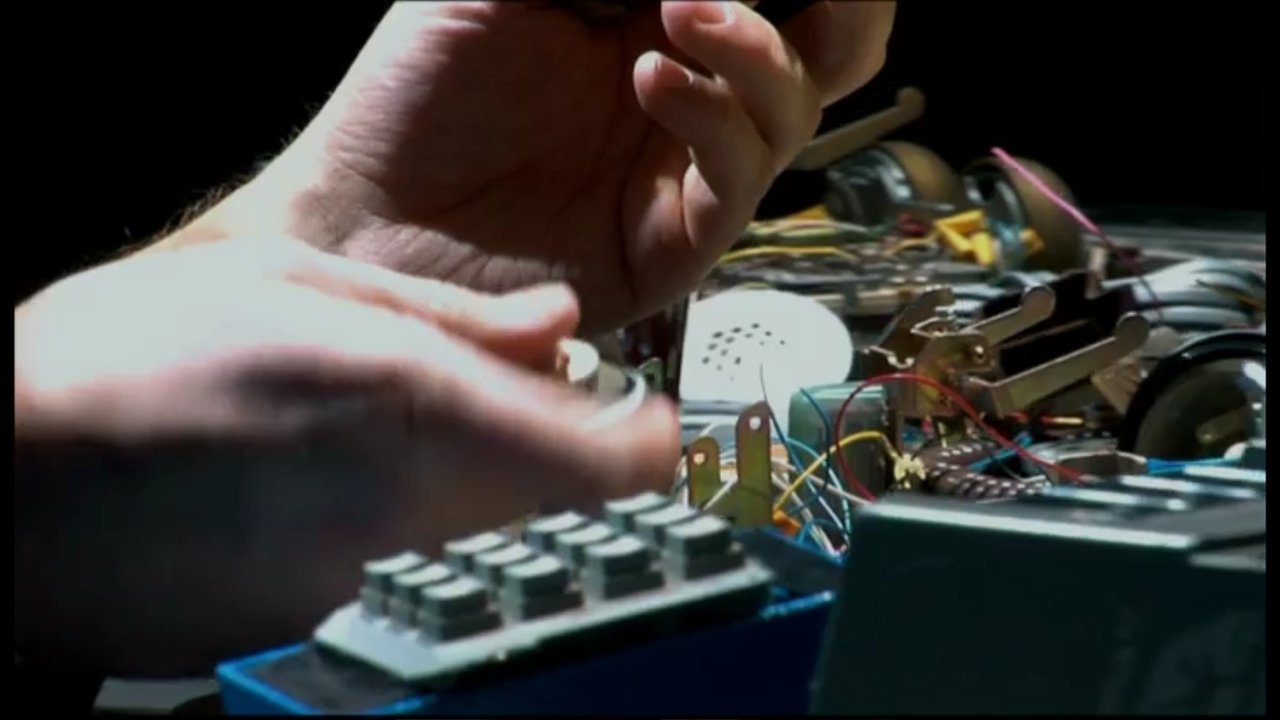
Code 2600(2011)
CODE 2600 documents the rise of the Information Technology Age as told through the events and people who helped build and manipulate it.
Movie: Code 2600
Top 10 Billed Cast
Herself
Herself
Herself
Himself
Himself
Himself
Himself
Himself
Himself
Himself
Video Trailer Code 2600
Recommendations Movies
 7.0
7.0Art & Copy(en)
The personal odysseys of some of the most influential advertising visionaries of all time and the stories behind their campaigns.
 7.3
7.3John Wick: Chapter 2(en)
John Wick is forced out of retirement by a former associate looking to seize control of a shadowy international assassins’ guild. Bound by a blood oath to aid him, Wick travels to Rome and does battle against some of the world’s most dangerous killers.
 6.2
6.2Halloween 4: The Return of Michael Myers(en)
Ten years after his original massacre, the invalid Michael Myers awakens on Halloween Eve and returns to Haddonfield to kill his seven-year-old niece.
 7.6
7.6Ex Machina(en)
Caleb, a coder at the world's largest internet company, wins a competition to spend a week at a private mountain retreat belonging to Nathan, the reclusive CEO of the company. But when Caleb arrives at the remote location he finds that he will have to participate in a strange and fascinating experiment in which he must interact with the world's first true artificial intelligence, housed in the body of a beautiful robot girl.
 7.6
7.6Avatar: The Way of Water(en)
Set more than a decade after the events of the first film, learn the story of the Sully family (Jake, Neytiri, and their kids), the trouble that follows them, the lengths they go to keep each other safe, the battles they fight to stay alive, and the tragedies they endure.
 6.8
6.8Eden Lake(en)
When a young couple goes to a remote wooded lake for a romantic getaway, their quiet weekend is shattered by an aggressive group of local kids. Rowdiness quickly turns to rage as the teens terrorize the couple in unimaginable ways, and a weekend outing becomes a bloody battle for survival.
 6.9
6.9Barbie(en)
Barbie and Ken are having the time of their lives in the colorful and seemingly perfect world of Barbie Land. However, when they get a chance to go to the real world, they soon discover the joys and perils of living among humans.
 8.1
8.1Soul(en)
Joe Gardner is a middle school teacher with a love for jazz music. After a successful audition at the Half Note Club, he suddenly gets into an accident that separates his soul from his body and is transported to the You Seminar, a center in which souls develop and gain passions before being transported to a newborn child. Joe must enlist help from the other souls-in-training, like 22, a soul who has spent eons in the You Seminar, in order to get back to Earth.
 6.3
6.3Atlantis: Milo's Return(en)
Milo and Kida reunite with their friends to investigate strange occurances around the world that seem to have links to the secrets of Atlantis.
 6.6
6.6Blue Beetle(en)
Recent college grad Jaime Reyes returns home full of aspirations for his future, only to find that home is not quite as he left it. As he searches to find his purpose in the world, fate intervenes when Jaime unexpectedly finds himself in possession of an ancient relic of alien biotechnology: the Scarab.
 5.6
5.6Darkman II: The Return of Durant(en)
Darkman and Durant return and they hate each other as much as ever. This time, Durant has plans to take over the city's drug trade using high-tech weaponry. Darkman must step in and try to stop Durant once and for all.
 6.9
6.9King of Beggars(cn)
The heir to a noble and influential family finds the love of his life, but she will only accept him if he becomes a kung-fu master. He becomes a legendary folk hero who tries to save the emperor.
 7.7
7.7All Quiet on the Western Front(de)
Paul Baumer and his friends Albert and Muller, egged on by romantic dreams of heroism, voluntarily enlist in the German army. Full of excitement and patriotic fervour, the boys enthusiastically march into a war they believe in. But once on the Western Front, they discover the soul-destroying horror of World War I.
 5.8
5.8Alvin and the Chipmunks(en)
A struggling songwriter named Dave Seville finds success when he comes across a trio of singing chipmunks: mischievous leader Alvin, brainy Simon, and chubby, impressionable Theodore.
 6.2
6.2The Return of Jafar(en)
The evil Jafar escapes from the magic lamp as an all-powerful genie, ready to plot his revenge against Aladdin. From battling elusive villains atop winged horses, to dodging flames inside an exploding lava pit, it's up to Aladdin - with Princess Jasmine and the outrageously funny Genie by his side - to save the kingdom once and for all.
 5.5
5.5Don't Knock Twice(en)
A mother desperate to reconnect with her troubled daughter becomes embroiled in the urban legend of a demonic witch.
![[REC]⁴ Apocalypse](https://image.tmdb.org/t/p/w300/nlSSZNESHkY1iPzYnpcRvYUr7Mz.jpg) 5.6
5.6[REC]⁴ Apocalypse(es)
Ángela Vidal, the young television reporter who entered the building with the firemen, manages to make it out alive. But what the soldiers don't know is that she carries the seed of the strange infection. She is to be taken to a provisional quarantine facility, a high-security installation where she will have to stay in isolation for several days. An old oil tanker, miles off shore and surrounded by water on all sides, has been especially equipped for the quarantine.
 6.1
6.1xXx: Return of Xander Cage(en)
Xander Cage is left for dead after an incident, though he secretly returns to action for a new, tough assignment with his handler Augustus Gibbons.
Similar Movies
 8.0
8.0Tracking Russian Hackers(fr)
Amid the growing threat of cyberattacks from Russian hackers, this film dives into their origins, motives, and the dangers they pose to their targets.
 6.1
6.1Hackers Are People Too(en)
A portrait of the hacking community. In an effort to challenge preconceived notions and media-driven stereotypes Hackers Are People Too lets hackers speak for themselves and introduce their community to the public.
 9.0
9.0All Creatures Welcome(de)
All Creatures Welcome explores the world of hackers and nerds at the events of the Chaos Computer Club, Europe's largest hacker association. The film dispels common clichés and draws a utopian picture of a possible society in the digital age.
 8.0
8.0A Dangerous Boy(en)
Sigurdur Thordarson, known as Siggi, becomes a hacker at 12, exposing Icelandic bank corruption at 14. Branded the "teenage whistleblower," he joins WikiLeaks in 2010, mentored by Julian Assange. Siggi leaks globally, but clashes with Assange, prompting him to spy for the FBI at 18. This tale weaves paranoia, hacking, and friendship, portraying Siggi's turbulent journey from trust to betrayal, revealing a heart-wrenching coming-of-age narrative.
 6.9
6.9Freedom Downtime(en)
A feature-length documentary about the Free Kevin movement and the hacker world.
 7.0
7.0Revolution OS(en)
REVOLUTION OS tells the inside story of the hackers who rebelled against the proprietary software model and Microsoft to create GNU/Linux and the Open Source movement.
 6.8
6.8The Crazy Che(es)
The incredible story of Bill Gaede, an Argentinian engineer, programmer… and Cold War spy.
 8.0
8.0Click to Ransom(en)
A small rural hospital in Japan battles an international cybercriminal gang that is holding them ransom with their stolen patient data.
 0.0
0.0Hacking at Leaves(en)
Hacking at Leaves documents artist and hazmat-suit aficionado Johannes Grenzfurthner as he attempts to come to terms with the United States' colonial past, Navajo tribal history, and the hacker movement. The story hones in on a small tinker space in Durango, Colorado, that made significant contributions to worldwide COVID relief efforts. But things go awry when Uncle Sam interferes with the film's production.
 6.4
6.4In the Realm of the Hackers(en)
In The Realm of the Hackers is a documentary about the prominent hacker community, centered in Melbourne, Australia in the late 80's to early 1990. The storyline is centered around the Australian teenagers going by the hacker names "Electron" and "Phoenix", who were members of an elite computer hacking group called The Realm and hacked into some of the most secure computer networks in the world, including those of the US Naval Research Laboratory, Lawrence Livermore National Laboratory, a government lab charged with the security of the US nuclear stockpile, and NASA.
 7.2
7.2Putin's Bears - The Most Dangerous Hackers in the World(de)
They call themselves Fancy Bear, Cozy Bear or Voodoo Bear. Elite units of the Russian secret services are hidden behind these code names. They are among the most dangerous hackers in the world. The bears were already in the computer of then-Chancellor Angela Merkel in 2015, interfered in the US election campaign in 2016 and are currently influencing the war in Ukraine. The makers of the successful YouTube channel “Simplicissimus” in co-production with funk and SWR are back and show the destructive potential of state hacking with this documentary. With the help of leading German hackers, cyberspace experts and a lot of humor, they delicately demystify the Russian bears: Who are the people behind them? How do they operate? And what makes them so incredibly dangerous?
 7.6
7.6Hacking Democracy(en)
Documentary film investigating allegations of election fraud during the 2004 U.S. presidential election. Electronic voting machines count approximately 90% of America's votes in county, state and federal elections. The technology is also increasingly being used across the world, including in Canada, the United Kingdom, Europe and Latin America. The film uncovers incendiary evidence from the trash cans of Texas to the ballot boxes of Ohio, exposing secrecy, votes in the trash, hackable software and election officials rigging the presidential recount.Ultimately proving our votes can be stolen without a trace "Hacking Democracy" culminates in the famous 'Hursti Hack'; a duel between the Diebold voting machines and a computer hacker from Finland - with America's democracy at stake.
 6.3
6.3Defeating the Hackers(en)
Exploring the murky and fast-paced world of the hackers out to steal money and identities and wreak havoc with people's online lives, and the scientists who are joining forces to help defeat them.
 6.5
6.5The 414s(en)
THE 414s tells the story of the first widely recognized computer hackers, a group of Milwaukee teenagers who gained notoriety in 1983 when they broke into dozens of high-profile computer systems, including the Los Alamos National Laboratory, a classified nuclear weapons research facility.
 7.5
7.5Pirat@ge(fr)
The documentary Pirat@ge traces the history of the Internet through the testimonies of those who built it: the hackers. It delves into the concerns of Generation Y, analyzing their networked communication methods, cultural consumption habits, and the sharing of such content.
 7.2
7.2TPB AFK: The Pirate Bay - Away from Keyboard(sv)
TPB AFK is a documentary about three computer addicts who redefined the world of media distribution with their hobby homepage The Pirate Bay. How did Tiamo, a beer crazy hardware fanatic, Brokep a tree hugging eco activist and Anakata – a paranoid hacker libertarian – get the White House to threaten the Swedish government with trade sanctions? TPB AFK explores what Hollywood’s most hated pirates go through on a personal level.
 5.0
5.0Hackers in Wonderland(en)
Hackers in Wonderland is a 2000 documentary film, produced and directed by Russell Barnes, about hackers in the United Kingdom.
 0.0
0.0Russia's Cyber Army(ru)
For years now, the Kremlin has been systematically trying to use well-trained hackers for its own benefit. In exchange for freedom and protection, they do the dirty work of the state, interfering in other countries’ elections and penetrating government networks. Just how dangerous is Russia’s cyber army?




